Bad Rabbit: A new ransomware epidemic is on the rise
WHAT IS BAD RABBIT? RANSOMWARE PARALYZES TRAIN STATIONS, AIRPORTS AND MEDIA IN RUSSIA AND EUROPE
What is known at the moment is that Bad Rabbit ransomware has infected several big Russian media outlets, with Interfax news agency and Fontanka.ru among the confirmed victims of the malware. Odessa International Airport has reported on a cyberattack on its information system, though whether it’s the same attack is not yet clear.
What is Bad Rabbit Ransomware?
Ransomware attacks are on the rise and, the recent one that’s making headlines this week is the Bad Rabbit Ransomware. The malware is said to be linked to the previously released Petya ransomware and inspired by Game of Thrones as the code contains references to the Dragons featured in it.
Bad Rabbit ransomware has affected corporate and media houses in Russia and Ukraine and appears to be affecting Turkey and Germany. Though the full reach and extent of it is yet to be determined, researchers at Kaspersky security firm say that Bad Rabbit ransomware bears resemblance to WannaCry and Petya outbreaks earlier this year.
The head of Russian cybersecurity firm Group – IB, Ilya Sachkov told, “In some companies, work has been completely paralysed as servers and workstations are encrypted.” Some of the affected systems are the airport in Ukraine, the underground railway in capital city, Kiev and several Russian websites like Interfax news agency and Fontanka.ru
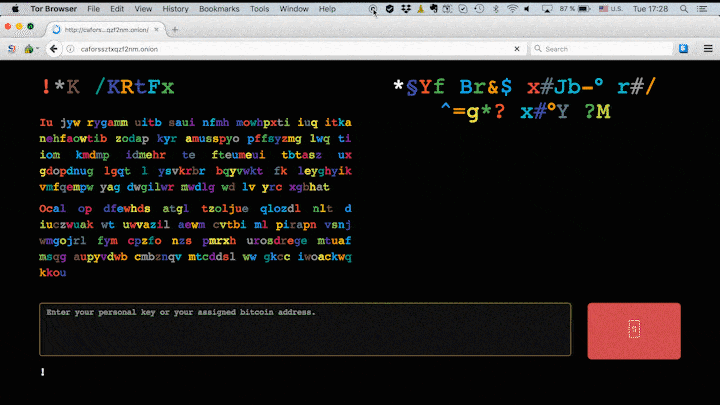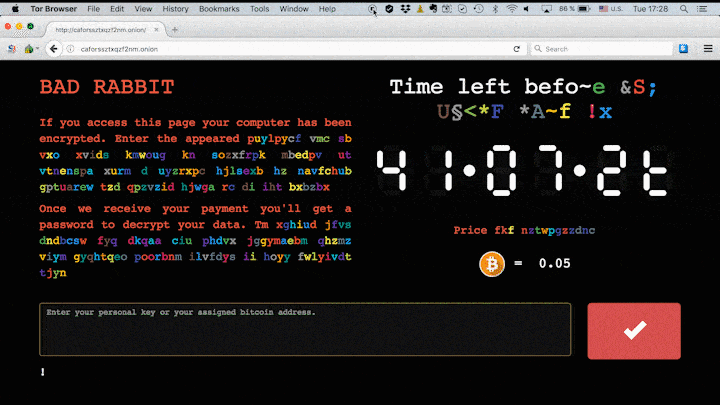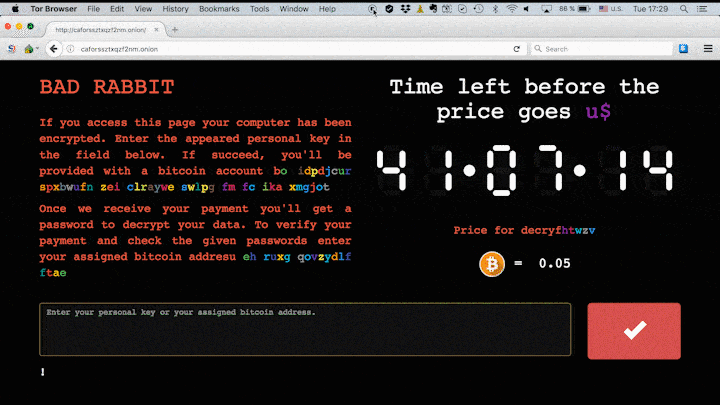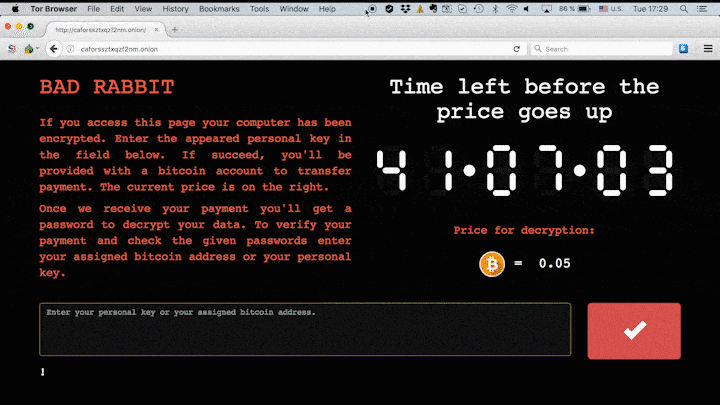
The criminals behind the Bad Rabbit attack are demanding 0.05 bitcoin as ransom — that’s roughly $280 at the current exchange rate.
Bad Rabbit Ransomware: How does it work?
It is a drive-by attack: Victims download a fake Adobe Flash installer from infected websites and manually launch the .exe file, thus infecting themselves. a number of compromised websites, all news or media sites. most of the victims of these attacks are located in Russia. We have also seen similar but fewer attacks in Ukraine, Turkey, and Germany. This ransomware has infected devices through a number of hacked Russian media websites. Based on experts’ investigation, this is a targeted attack against corporate networks, using methods similar to those used in the ExPetr attack.
experts have collected enough evidence to link the Bad Rabbit attack with the ExPetr attack, which happened in June of this year. According to their analysis, some of the code used in Bad Rabbit was previously spotted in ExPetr.
Other similarities include the same list of domains used for the drive-by attack (some of those domains were hacked back in June but not used) as well as the same techniques used for spreading the malware throughout corporate networks — both attacks used Windows Management Instrumentation Command-line (WMIC) for that purpose. However, there is a difference: Unlike ExPetr, Bad Rabbit doesn’t use the EternalBlue exploit — or any other exploit.
As opposed to the other malwares, Bad Rabbit ransomware requires the victims to download a fake Adobe Flash Installer and manually run the .exe file. When this happens, the malware encrypts the contents of the computer system, thus infecting the system. Once the encryption is complete it asks for a ransom payment of 0.05 bitcoins that’s close to $280 USD. The screen shows the hour as 41 hours and if the victims do not pay within the specified time limit, the ransom amount keeps on going up.
According to Kaspersky researchers, “This is a targeted attack against corporate networks, using methods similar to those used in the ExPetr attack.” According to their investigation, a bit of the code used in Bad Rabbit ransomware was previously spotted in Petya. But unlike Petya ransomware, Bad Rabbit doesn’t use exploits and needs to be manually run. Also, it uses a Trojan like Mimikatz tool to extract data from affected systems.
How to Keep Safe?
Most IMPORTANT is not to download the Adobe Flash Installer from any other website or links on email, apart from the official Adobe website, as the ransomware only infects the system if the fake Adobe Flash player is manually installed.
Bad Rabbit works by holding the infected computers and networks to ransom before spreading in a “worm-like fashion” to other computers.
CLICK HERE for procedure to immunize your computer system.
Victims of Bad Rabbit
Victims of the Bad Rabbit ransomware include the Kiev Metro and Odessa International Airport in Ukraine, as well as Russian news agency Interfax and other media organisations.
Recommendations:
Always be cautious when clicking links on the internet as well as any unknown or suspicious emails
(1) Don’t open emails from unknown senders.
(2) Don’t click on links sent to you by email or on the internet.
(2) Download Adobe Flash Player only from the official Adobe website and not any other source
(4) Update your antivirus and scan your system regularly.
(5) If you notice anything out of normal activity on your system, do reach out to your IT help Assistance desk immediately
References:
https://www.cybereason.com/blog/cybereason-researcher-discovers-vaccine-for-badrabbit-ransomware
www.pushtiwebindia.com
www.pushti.in
www.incabrescia.com
www.seospecialistmumbai.com